# What is API
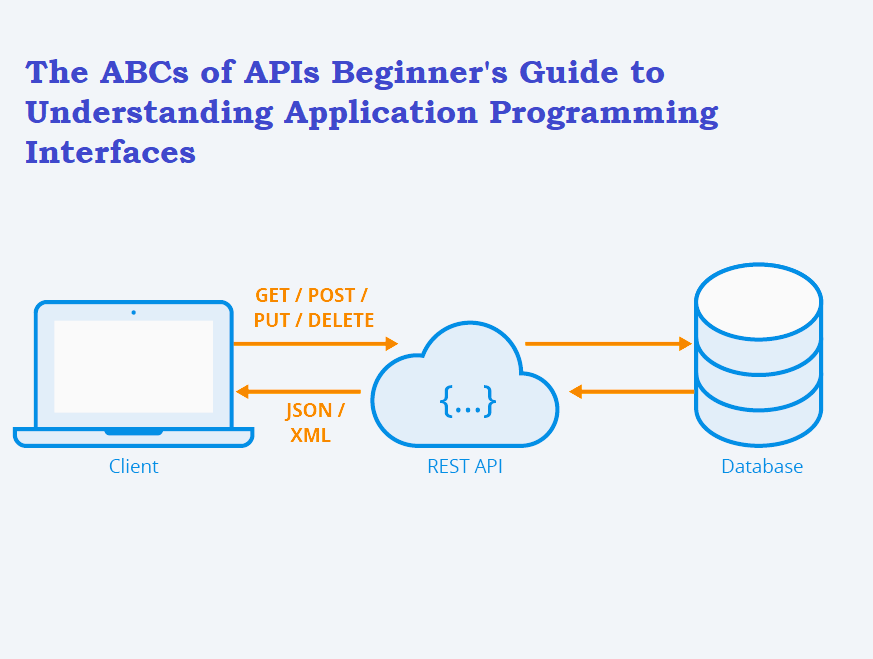
In this post, we will learn about What is API in detail. An API ( Application Programming Interface ) is a set of definitions and set of protocols that allow technology and services to communicate via the internet.
Similar to a messenger, APIs (Application Programming Interface) enables communication between various software programs. Imagine it as a restaurant waiter. Customers place orders with the waiter (applications), who then relays those orders to the kitchen (or other software systems) and returns the food to the diners (data or outcomes).
# API Call –
Api Call is the process of sending request to your API after setting up the right endpoints . It processes upon receiving your information and then you receive feedback .
Example- Entering login ID and password into a Application or website and hitting ‘Submit’ button , you made an API Call.
# API Endpoint –
API Endpoint is the end of a communication channel. When they interact with other system , each touchpoint of interaction is considered an endpoint. Generally it could be a server ,a service or a database where a resource lives.
# Integration –
API integration simply connect two or more Applications to exchange data between them and connect to the outside world.
# API Gateway –
An API gateway is an management tool that serves as an intermediary between the client and a set of different backend services. API gateways act as gatekeepers and proxies that moderate all your API Calls , aggregate the data you need, and return the expected results. Also we use Gateways to handle common tasks e.g API identification ,rate limitation, and usage metrics.
# API Lifecycle –
API lifecycle is an approach to API development that aims at providing a holistic view of how to manage APIs across its different stages, from creation to retirement. Also Life cycle of Apis divided into three stages, creation stage , control stage , and the consumption stage.
#API Request –
Consider an API request as a means of communication between developers and a server or database. Developers just need to add a particular endpoint to a URL when they wish to fetch or transfer data from their application. On the server or database that has the necessary information, this endpoint serves as a destination. It resembles dialing a phone number to reach a certain individual.
Developers can ask the server or database for the data they want or even submit fresh data by using this endpoint in their API request. It is comparable to making a request at a restaurant when the server communicates your request to the kitchen.
HTTP Request –
HTTP request sent by a client to a server to retrieve or modify data , a request typically includes a base URL(domain), method name ,set of headers and body parameters.
Payload –
the important data which is send or transferred across several systems
When we talk about the “payload,” we’re referring to the important data which is send or transferred across several systems. We use JSON objects frequently to organize this data.
The format most commonly used for displaying structured data is JSON (JavaScript Object Notation).
HTTP Response –
Consider that you’re requesting some information from a buddy in a message. Your buddy reads your message when they get it and replies with the details you asked for. Similar to this, a server addresses a request sent by a client (such as a web browser or a mobile app) and replies with an answer (HTTP Response).
Response Code –
A numerical status code that is returned in an API response to show whether a request was successful or unsuccessful. Response codes that are often used include 200 (OK), 404 (Not Found), and 500 (Internal Server Error).
API Keys –
An API key is similar to a unique pass that enables various applications to identify and validate users, developers, or other API calling software. Imagine it as a special ID that serves as a virtual ID card.
For e.g. how we require a key to open a door. API keys act as the key that permits access to particular features or services. Before giving access to certain services or data, they allow software programs to verify and authenticate the identity of the requester.
A developer creating a mobile application that accesses a weather API to obtain weather data. Firstly, you need an API key to use the services offered by the API. This key serves as your digital ID, demonstrating your legitimacy as a user.
# There are several uses for APIs:
- Integration: APIs enable smooth collaboration across many apps. They basically make it simpler to link systems and communicate information by allowing apps to share data and functionality.
- Third-party apps: Using APIs, programmers may build new apps that access the functions and also information of current platforms. For instance, social media APIs enable developers to create apps that communicate with social media sites like Twitter or Facebook.
- Improving Software Capabilities: APIs provide apps new features. In their own apps, programmers may incorporate services i.e. maps, weather information, payment processors, or even sophisticated algorithms like machine learning.
- Mobile App Development: APIs are essential to the creation of mobile apps. They enable interaction between mobile apps and backend services.
# Remember when creating a secure API:
- Authorization and Authentication: APIs must make sure that only approved users or apps may access their services. This is accomplished through the use of authentication, in which users demonstrate their identity (for example, by displaying an ID card), and authorization, which manages access to certain resources or actions.
- Encryption: To avoid unwanted access, APIs should encrypt the data they transfer over the network. To ensure that only the intended receiver can comprehend the information being communicated, it’s like utilizing a secret code.
- Input Validation: To prevent security problems, APIs must verify and clean the data they receive. The analogy would be to inspect and clean the food ingredients before using them to avoid infection.
- Rate Limiting: APIs should have controls in place to restrict how many requests may come from a single client in a given period of time. This stops misuse and guarantees equitable use of the API’s resources.
- Error Handling: APIs must correctly handle errors to avoid disclosing sensitive data. Also It’s similar to telling a client respectfully that a meal is unavailable without divulging the kitchen’s top-secret recipes.
- Logging and Monitoring: APIs must log all activity and keep an eye out for any unauthorized or suspicious access attempts. This aids in spotting and addressing possible security problems.
- Regular Security upgrades: To address any vulnerabilities in the underlying software components, APIs should be kept up to date with security patches and upgrades.
- API Documentation: Developers should be given clear and thorough instructions on how to use the API safely.